
Understanding Artificial Intelligence and Machine Learning in Cybersecurity
Machine learning and Artificial Intelligence have revolutionized nearly every modern industry, and more specifically have impacted the cybersecurity industry significantly. AI has taken cybersecurity to a whole new level, significantly improving its effectiveness and efficiency.
Before AI and ML integrations, cybersecurity relied on traditional rule-based methods and manual analysis. With rule-based methods and algorithms, they very often fall short, unable to keep pace with the rapidly evolving cyber threats.
AI and ML’s key advantage in cybersecurity lies in their ability to analyze vast amounts of data and detect patterns indicative of malicious activities. Traditional methods often struggled with the sheer volume and complexity of data generated by various sources, sometimes reaching millions of daily transactions. Machine learning algorithms excel at processing and analyzing such data, enabling the detection of subtle and sophisticated threats that conventional methods may miss.
The process remains similar: models are trained on large labeled datasets containing both normal and malicious behaviors. Once trained this enables cyber security algorithms to adapt to new threats, continuously improving their ability to detect and respond to cyberattacks. By harnessing machine learning, cybersecurity systems gain a better understanding of the evolving threat landscape, strengthening their proactive defense mechanisms. Now, let's explore real-life applications of AI in cybersecurity.
AI and Machine Learning for Fraud Detection & Prevention
In fraud detection, an AI or machine learning model is trained on a vast dataset of user actions and behaviors. The model examines each user's behavioral patterns, distinguishing between normal and suspicious activities. This allows the model to classify future user actions into either the normal or suspicious category. To better explain the detection process, let's take an example of a banking system.
In a banking system, a normal set of actions and behaviors for a user typically includes:
- Login Behavior: Monitoring regular logins from familiar devices and associated IP addresses, along with consistent login times, like during business hours or specific patterns.
- Multiple login attempts with incorrect credentials
- Odd login attempts at suspicious locations outside of regular location
- Transaction Behavior: Identifying consistent transaction types and amounts based on the user's historical data. Paying attention to transactions within the user's known geographical areas or common patterns.
- Unusually large transactions or sudden spikes in spending
- abnormal patterns of transactions
- Transactions made at untrusted merchants
- Account Management: Regularly checking updates or modifications to personal information within reasonable limits, like password changes, email updates, or address changes.
- Numerous and frequent changes to personal information
- Suspicious attempts to add unauthorized beneficiaries or modify payees.
-
Card Usage: Noticing consistent card usage patterns, such as frequent usage at preferred merchants or specific transaction types like online purchases or ATM withdrawals.
- Unusual card activity (multiple high-value transactions in quick succession) or card usage from geographically distant locations.
When a new transaction or action occurs, the model compares it to the learned patterns of normal behavior. If the new action aligns with established patterns, it's classified as normal. However, if the action significantly deviates from the learned patterns, it's flagged as potentially suspicious, triggering further investigation. Could be as simple as a text for verifications, card decline and confirmation of charge, or even a temporary lock on an account or card.
AI and Machine Learning to Prevent Phishing and Spam Detection
Similar to fraud detection, phishing and spam detection using machine learning involves training a model on a large dataset of emails, distinguishing between legitimate and fraudulent/spam emails. The model analyzes various features and patterns within the email data to identify indicators of phishing attempts and spam.
Now let's delve into the detection process identifying what is considered either spam or a non-spam email and what patterns the model follows in differentiating between the two.
| Normal Email Patterns: | Suspicious Email Patterns: | |
|---|---|---|
| Email Content | Relevant content, consistent language, and include links or attachments from trusted sources. | Lack personalization, request urgent personal or financial information, and exhibit poor grammar or unusual language patterns. |
| Sender Information | From known contacts or reputable organizations using trusted domains. | Use slight variations or misspellings of reputable organizations' email addresses and come from unrecognized or suspicious domains. |
| Structural Elements | Proper formatting, correct header information, and consistent email signatures or company branding. | Have missing or manipulated header information, inconsistent email signatures, or lack proper formatting. |
| User Interactions | Legitimate emails involve regular interactions, such as replies and clicks on embedded links, aligning with expected frequency based on historical data. | Lack of previous interactions and containing unexpected or out-of-context communication compared to historical data, raising concerns for further verification. |
By analyzing these patterns and features, machine learning models can classify incoming emails as either legitimate or potentially phishing attempts and spam. The models learn from historical data to identify common characteristics and indicators of fraudulent or spammy emails. This learned knowledge enables the model to identify new and suspicious emails based on the patterns it has been trained on.
Malware Detection with AI and Machine Learning Models
Malware detection using AI involves training a machine learning model on a diverse dataset of known malware samples and legitimate files. The attributes and details of known malware can be extrapolated to other unknown attacks. Let's explore the detection process and how the model differentiates attacks:
- File Attributes: Legitimate files possess attributes consistent with their file type, including correct file extensions, accurate metadata, and appropriate header information associated with the file format. Files from trusted sources or reputable publishers are typically categorized as legitimate.
- Unusual or suspicious file extensions or name alterations in suspicious files
- Missing or manipulated metadata, incorrect file formats, or mismatches
- Files from unknown or suspicious sources
- Code Analysis: Legitimate files contain binary code that adheres to anticipated patterns and structures. They often come with valid digital signatures or certificates from trusted authorities. Additionally, their use of APIs and libraries aligns with the file's intended purpose.
- Use of obfuscated or encrypted code to evade detection
- Lack of validity, missing digital signatures, or certificates
- Utilization of unauthorized or known malicious APIs and libraries
- Behavior Analysis: Legitimate files exhibit expected behavior when executed or interacted with. They make standard system calls, engage in network communications within acceptable limits, and conventionally use system resources. Legitimate files do not display suspicious activities such as unauthorized access or attempts to modify critical system files.
- Unexpected or abnormal behavior during execution
- Attempts to modify system files or establish unauthorized network connections
- Excessive resource consumption
- Unauthorized access to sensitive data
- Attempts to exploit vulnerabilities
By analyzing these patterns and features, machine learning models can classify files as either legitimate or potentially malicious. The models learn from historical data to identify common characteristics and indicators of malware. This learned knowledge enables the model to identify new and previously unseen malware instances based on the patterns it has been trained on.
Configure your next multi-GPU Deep Learning Workstation for developing complex AI models featuring the NVIDIA RTX 6000 Ada.
Challenges and Limitations of Using AI and Machine Learning in Cybersecurity
False Positives and False Negatives: Machine learning models can produce false positives (classifying benign instances as malicious) or false negatives (failing to detect actual malicious instances). Striking the right balance between minimizing false alarms while maximizing detection rates is a challenge that requires careful fine-tuning and model evaluation.
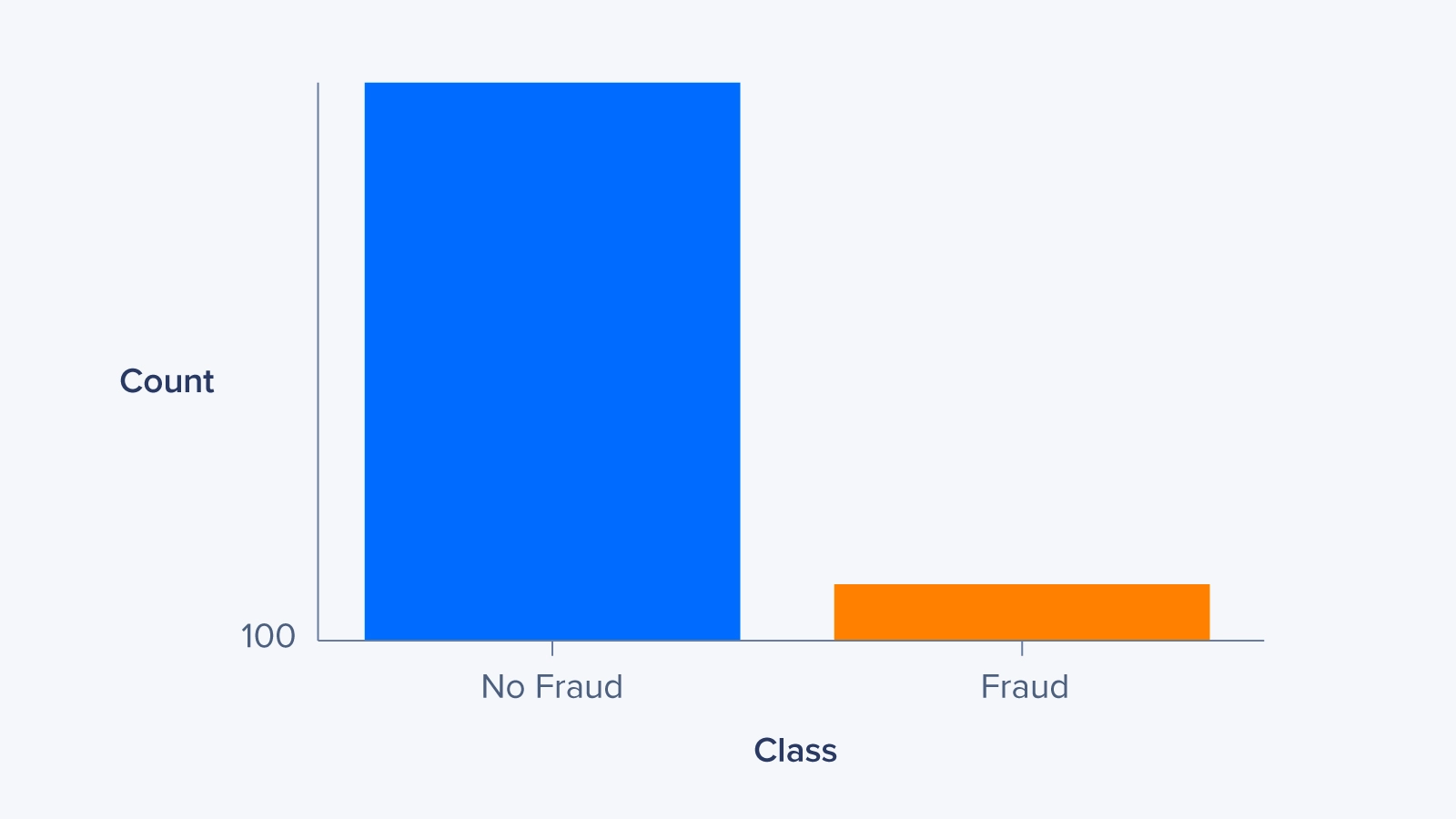
Feeding Imbalanced Data to a Model: In cybersecurity, the occurrence of malicious activities is typically much lower compared to normal or benign activities. This leads to imbalanced datasets where the number of positive (malicious) samples is significantly smaller than the negative (benign) samples. Imbalanced data can affect the model's ability to accurately detect rare events and may result in biased predictions.
Best Practices for Implementing AI and Machine Learning in Cybersecurity
Define Clear Cybersecurity Objectives
Clearly defining objectives is a crucial step when implementing any detection algorithm in cybersecurity. By outlining your goals and the challenges you want to address, you create a strong foundation for your strategy. This clarity helps you choose the right algorithms that align with your goals, ensuring you have the appropriate tools for the task.
Setting objectives also guides the data collection process. By understanding the specific issues, you can gather relevant and representative datasets that capture the intricacies of cybersecurity threats. This high-quality data is essential for effectively training your machine learning models.
Well-defined objectives result in reliable measures of success for your new implementations; establish performance metrics and define evaluation methods to help gauge your models' performance in achieving the desired outcomes. This feedback loop allows you to refine your approach, make improvements, and fine-tune your cybersecurity ML model.
Collect High-Quality Training Data for your Cybersecurity AI/ML Model
Gathering high-quality data is the most important step for effective AI and machine learning training. High-quality data is accurate, comprehensive, and appropriately labeled data encompassing various aspects of security incidents, threats, or network behavior.
For instance, when developing a model to detect a Distributed Denial of Service (DDoS) attack, it is crucial to gather network traffic data from diverse sources, good and bad. The dataset should faithfully capture both normal network behavior and instances of DDoS attacks ranging from attack vectors, sizes, durations, and network topologies to enable the model to distinguish between benign and malicious traffic patterns adeptly.
Clean data that is comprehensible is just as crucial and proper labeling helps indicate whether a network traffic instance corresponds to benign or malicious activity. Skilled cybersecurity analysts can manually label the data, or automated techniques can also be used. You can also use generative AI to generate synthetic data based on previous attacks to further train and test your model.
By accumulating high-quality data that faithfully represents real-world cybersecurity scenarios, the machine learning model establishes a robust foundation for learning attack patterns. This, in turn, facilitates generalization and accurate predictions within live network environments.
Continuously Monitor & Improve Cybersecurity Efforts
Cyber attackers will continually try to outsmart your system thus the need for continual monitoring and improvement in cybersecurity becomes critical. Fraudsters and hackers are perpetually evolving their tactics, techniques, and procedures to bypass existing security measures and exploit vulnerabilities. Organizations must adapt and enhance their defenses accordingly as they change their styles and behaviors.
Continuously monitoring a company’s cybersecurity efforts allows organizations to keep a close eye on emerging fraud patterns and the evolving techniques employed by hackers. By analyzing network traffic, system logs, and security events in real-time, organizations can identify new attack vectors and patterns of suspicious activities. This proactive approach enables the detection of fraudulent behavior that might go unnoticed by traditional rule-based systems.
In the world of cybersecurity, cybersecurity engineers must understand that what may be effective today may not work tomorrow.
Final Thoughts on Artificial Intelligence in Cybersecurity
Machine learning has emerged as a game-changer revolutionizing the way organizations detect and respond to threats. While challenges like imbalanced data and adversarial attacks persist, they can be overcome through responsible implementation and collaboration within the cybersecurity community.
By implementing new and adaptive AI and machine learning algorithms and reinforcing security measures, organizations can bolster their defenses against ever-evolving threats. It is imperative that as your cybersecurity measures are developing AI to prevent attacks, it is also safe to assume and precautionary the idea that attackers are using AI to develop attacks. The creative utilization of machine learning in cybersecurity will persistently mold a secure digital landscape, safeguarding valuable assets, and staying ahead of cyber adversaries.
Check out other industries that AI has made an impact in here!
Exxact Corp. procures the highest-performing hardware for your next workstation or server used to train complex AI models and develop machine learning algorithms.
Contact us today or check out our various deep-learning platforms.

AI in Cybersecurity - Fraud Detection, Phishing, Malware
Understanding Artificial Intelligence and Machine Learning in Cybersecurity
Machine learning and Artificial Intelligence have revolutionized nearly every modern industry, and more specifically have impacted the cybersecurity industry significantly. AI has taken cybersecurity to a whole new level, significantly improving its effectiveness and efficiency.
Before AI and ML integrations, cybersecurity relied on traditional rule-based methods and manual analysis. With rule-based methods and algorithms, they very often fall short, unable to keep pace with the rapidly evolving cyber threats.
AI and ML’s key advantage in cybersecurity lies in their ability to analyze vast amounts of data and detect patterns indicative of malicious activities. Traditional methods often struggled with the sheer volume and complexity of data generated by various sources, sometimes reaching millions of daily transactions. Machine learning algorithms excel at processing and analyzing such data, enabling the detection of subtle and sophisticated threats that conventional methods may miss.
The process remains similar: models are trained on large labeled datasets containing both normal and malicious behaviors. Once trained this enables cyber security algorithms to adapt to new threats, continuously improving their ability to detect and respond to cyberattacks. By harnessing machine learning, cybersecurity systems gain a better understanding of the evolving threat landscape, strengthening their proactive defense mechanisms. Now, let's explore real-life applications of AI in cybersecurity.
AI and Machine Learning for Fraud Detection & Prevention
In fraud detection, an AI or machine learning model is trained on a vast dataset of user actions and behaviors. The model examines each user's behavioral patterns, distinguishing between normal and suspicious activities. This allows the model to classify future user actions into either the normal or suspicious category. To better explain the detection process, let's take an example of a banking system.
In a banking system, a normal set of actions and behaviors for a user typically includes:
- Login Behavior: Monitoring regular logins from familiar devices and associated IP addresses, along with consistent login times, like during business hours or specific patterns.
- Multiple login attempts with incorrect credentials
- Odd login attempts at suspicious locations outside of regular location
- Transaction Behavior: Identifying consistent transaction types and amounts based on the user's historical data. Paying attention to transactions within the user's known geographical areas or common patterns.
- Unusually large transactions or sudden spikes in spending
- abnormal patterns of transactions
- Transactions made at untrusted merchants
- Account Management: Regularly checking updates or modifications to personal information within reasonable limits, like password changes, email updates, or address changes.
- Numerous and frequent changes to personal information
- Suspicious attempts to add unauthorized beneficiaries or modify payees.
-
Card Usage: Noticing consistent card usage patterns, such as frequent usage at preferred merchants or specific transaction types like online purchases or ATM withdrawals.
- Unusual card activity (multiple high-value transactions in quick succession) or card usage from geographically distant locations.
When a new transaction or action occurs, the model compares it to the learned patterns of normal behavior. If the new action aligns with established patterns, it's classified as normal. However, if the action significantly deviates from the learned patterns, it's flagged as potentially suspicious, triggering further investigation. Could be as simple as a text for verifications, card decline and confirmation of charge, or even a temporary lock on an account or card.
AI and Machine Learning to Prevent Phishing and Spam Detection
Similar to fraud detection, phishing and spam detection using machine learning involves training a model on a large dataset of emails, distinguishing between legitimate and fraudulent/spam emails. The model analyzes various features and patterns within the email data to identify indicators of phishing attempts and spam.
Now let's delve into the detection process identifying what is considered either spam or a non-spam email and what patterns the model follows in differentiating between the two.
| Normal Email Patterns: | Suspicious Email Patterns: | |
|---|---|---|
| Email Content | Relevant content, consistent language, and include links or attachments from trusted sources. | Lack personalization, request urgent personal or financial information, and exhibit poor grammar or unusual language patterns. |
| Sender Information | From known contacts or reputable organizations using trusted domains. | Use slight variations or misspellings of reputable organizations' email addresses and come from unrecognized or suspicious domains. |
| Structural Elements | Proper formatting, correct header information, and consistent email signatures or company branding. | Have missing or manipulated header information, inconsistent email signatures, or lack proper formatting. |
| User Interactions | Legitimate emails involve regular interactions, such as replies and clicks on embedded links, aligning with expected frequency based on historical data. | Lack of previous interactions and containing unexpected or out-of-context communication compared to historical data, raising concerns for further verification. |
By analyzing these patterns and features, machine learning models can classify incoming emails as either legitimate or potentially phishing attempts and spam. The models learn from historical data to identify common characteristics and indicators of fraudulent or spammy emails. This learned knowledge enables the model to identify new and suspicious emails based on the patterns it has been trained on.
Malware Detection with AI and Machine Learning Models
Malware detection using AI involves training a machine learning model on a diverse dataset of known malware samples and legitimate files. The attributes and details of known malware can be extrapolated to other unknown attacks. Let's explore the detection process and how the model differentiates attacks:
- File Attributes: Legitimate files possess attributes consistent with their file type, including correct file extensions, accurate metadata, and appropriate header information associated with the file format. Files from trusted sources or reputable publishers are typically categorized as legitimate.
- Unusual or suspicious file extensions or name alterations in suspicious files
- Missing or manipulated metadata, incorrect file formats, or mismatches
- Files from unknown or suspicious sources
- Code Analysis: Legitimate files contain binary code that adheres to anticipated patterns and structures. They often come with valid digital signatures or certificates from trusted authorities. Additionally, their use of APIs and libraries aligns with the file's intended purpose.
- Use of obfuscated or encrypted code to evade detection
- Lack of validity, missing digital signatures, or certificates
- Utilization of unauthorized or known malicious APIs and libraries
- Behavior Analysis: Legitimate files exhibit expected behavior when executed or interacted with. They make standard system calls, engage in network communications within acceptable limits, and conventionally use system resources. Legitimate files do not display suspicious activities such as unauthorized access or attempts to modify critical system files.
- Unexpected or abnormal behavior during execution
- Attempts to modify system files or establish unauthorized network connections
- Excessive resource consumption
- Unauthorized access to sensitive data
- Attempts to exploit vulnerabilities
By analyzing these patterns and features, machine learning models can classify files as either legitimate or potentially malicious. The models learn from historical data to identify common characteristics and indicators of malware. This learned knowledge enables the model to identify new and previously unseen malware instances based on the patterns it has been trained on.
Configure your next multi-GPU Deep Learning Workstation for developing complex AI models featuring the NVIDIA RTX 6000 Ada.
Challenges and Limitations of Using AI and Machine Learning in Cybersecurity
False Positives and False Negatives: Machine learning models can produce false positives (classifying benign instances as malicious) or false negatives (failing to detect actual malicious instances). Striking the right balance between minimizing false alarms while maximizing detection rates is a challenge that requires careful fine-tuning and model evaluation.
Feeding Imbalanced Data to a Model: In cybersecurity, the occurrence of malicious activities is typically much lower compared to normal or benign activities. This leads to imbalanced datasets where the number of positive (malicious) samples is significantly smaller than the negative (benign) samples. Imbalanced data can affect the model's ability to accurately detect rare events and may result in biased predictions.

Best Practices for Implementing AI and Machine Learning in Cybersecurity
Define Clear Cybersecurity Objectives
Clearly defining objectives is a crucial step when implementing any detection algorithm in cybersecurity. By outlining your goals and the challenges you want to address, you create a strong foundation for your strategy. This clarity helps you choose the right algorithms that align with your goals, ensuring you have the appropriate tools for the task.
Setting objectives also guides the data collection process. By understanding the specific issues, you can gather relevant and representative datasets that capture the intricacies of cybersecurity threats. This high-quality data is essential for effectively training your machine learning models.
Well-defined objectives result in reliable measures of success for your new implementations; establish performance metrics and define evaluation methods to help gauge your models' performance in achieving the desired outcomes. This feedback loop allows you to refine your approach, make improvements, and fine-tune your cybersecurity ML model.
Collect High-Quality Training Data for your Cybersecurity AI/ML Model
Gathering high-quality data is the most important step for effective AI and machine learning training. High-quality data is accurate, comprehensive, and appropriately labeled data encompassing various aspects of security incidents, threats, or network behavior.
For instance, when developing a model to detect a Distributed Denial of Service (DDoS) attack, it is crucial to gather network traffic data from diverse sources, good and bad. The dataset should faithfully capture both normal network behavior and instances of DDoS attacks ranging from attack vectors, sizes, durations, and network topologies to enable the model to distinguish between benign and malicious traffic patterns adeptly.
Clean data that is comprehensible is just as crucial and proper labeling helps indicate whether a network traffic instance corresponds to benign or malicious activity. Skilled cybersecurity analysts can manually label the data, or automated techniques can also be used. You can also use generative AI to generate synthetic data based on previous attacks to further train and test your model.
By accumulating high-quality data that faithfully represents real-world cybersecurity scenarios, the machine learning model establishes a robust foundation for learning attack patterns. This, in turn, facilitates generalization and accurate predictions within live network environments.
Continuously Monitor & Improve Cybersecurity Efforts
Cyber attackers will continually try to outsmart your system thus the need for continual monitoring and improvement in cybersecurity becomes critical. Fraudsters and hackers are perpetually evolving their tactics, techniques, and procedures to bypass existing security measures and exploit vulnerabilities. Organizations must adapt and enhance their defenses accordingly as they change their styles and behaviors.
Continuously monitoring a company’s cybersecurity efforts allows organizations to keep a close eye on emerging fraud patterns and the evolving techniques employed by hackers. By analyzing network traffic, system logs, and security events in real-time, organizations can identify new attack vectors and patterns of suspicious activities. This proactive approach enables the detection of fraudulent behavior that might go unnoticed by traditional rule-based systems.
In the world of cybersecurity, cybersecurity engineers must understand that what may be effective today may not work tomorrow.
Final Thoughts on Artificial Intelligence in Cybersecurity
Machine learning has emerged as a game-changer revolutionizing the way organizations detect and respond to threats. While challenges like imbalanced data and adversarial attacks persist, they can be overcome through responsible implementation and collaboration within the cybersecurity community.
By implementing new and adaptive AI and machine learning algorithms and reinforcing security measures, organizations can bolster their defenses against ever-evolving threats. It is imperative that as your cybersecurity measures are developing AI to prevent attacks, it is also safe to assume and precautionary the idea that attackers are using AI to develop attacks. The creative utilization of machine learning in cybersecurity will persistently mold a secure digital landscape, safeguarding valuable assets, and staying ahead of cyber adversaries.
Check out other industries that AI has made an impact in here!
Exxact Corp. procures the highest-performing hardware for your next workstation or server used to train complex AI models and develop machine learning algorithms.
Contact us today or check out our various deep-learning platforms.




.jpg?format=webp)